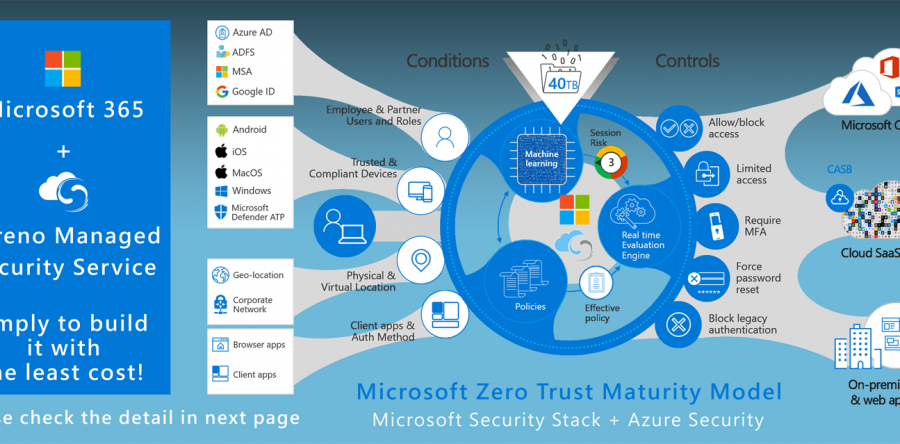
High levels of business security have become increasingly elusive as the threat landscape evolves and firms engage on a range of digital transformation projects. We have frequently responded to each new danger with a new tool or technology as an industry, with many firms implementing upwards of 100 different security solutions on average. There has been a lot of buzz around Zero Trust recently, but definitions and facts differ. As a result, many security experts are unsure how to put this new security philosophy into practice in their organizations. At its foundation, Zero Trust aims to eradicate implicit trust throughout the company by authenticating all digital transactions on a constant basis. This is a considerably more secure technique by definition, and it aids in the detection of some of the most complex and severe threats, such as ransomware and related behaviors like lateral movement. Organizations can now transform into Zero Trust enterprises by adopting a holistic strategy and implementing Zero Trust best practices across people, apps, and infrastructure. Through the consolidation of capabilities, the unification of security policy, and more consistent enforcement, this leads in improved levels of overall security and a decrease in complexity.
Users are subjected to "Least Access" policies.
When it comes to building a Zero Trust company, securing users through Zero Trust best practices is typically a smart place to start. This involves emphasis on strong identity best practices like multi-factor authentication implementation (MFA). Implicit trust for user devices must be avoided, and good endpoint protection should be used to limit the dangers associated with hacked devices. This is also where you implement "least access" through role-based access control policies that only provide each employee or position access to the resources they need to do their work.
Allowing for a Secure Cloud Migration
Although many businesses begin their Zero Trust journey by concentrating on users, it is as important to apply Zero Trust concepts to apps. In reality, several firms have run into roadblocks in their cloud migration owing to security vulnerabilities discovered late in the process. As a result, they are compelled to postpone several of their cloud efforts. To maintain the security and integrity of code and workloads such as hosts, containers, Kubernetes, and serverless operations, Zero Trust should be applied to applications. This includes recommended practices like using microsegmentation on cloud workloads to prevent lateral movement if a single resource is compromised.
Managing Supply Chain Risks and the Internet of Things
Supply chain resources and unmanaged infrastructure, such as IoT, are two further areas that are frequently disregarded. Vendors in the supply chain should be required to provide the security and Zero Trust policies that apply to their service. Vendors should not be assumed to be in charge of security. Security concerns and adherence to Zero Trust best practices should be assessed for each solution. Due to vast vulnerabilities, little to no built-in security, and a lack of solutions when it comes to robust authentication and endpoint protection, unmanaged devices continue to pose a serious danger with the growing rise of the Internet of Things (IoT).
Organizations should verify that they have complete insight into these devices and then assign "least access" rights to them in the same manner that they do to users. Policies for IoT devices might be quite restricted since they serve a very particular role inside the enterprise (think security camera or MRI machine). Security cameras should only be capable of speaking video protocols, connecting with video storage infrastructure, and downloading firmware upgrades from the internet.
The SOC's Role in Continuous Monitoring: Getting It Right
Continuous monitoring and improvement are critical to the maturation of any Zero Trust plan once businesses have strong visibility and have built solid Zero Trust rules. The Security Operations Center plays a critical role here, since it serves as a continuous audit function for Zero Trust regulations. To enable continual security analytics and correlation of complex, multi-faceted security events, telemetry from the whole set of security tools and capabilities should be used. This verifies that the Zero Trust controls are accurate and that any security vulnerabilities in the policy are closed.
Creating a Roadmap to a Zero-Trust Business